Windows恶意软件BazarLoader分析
责编:gltian |2021-10-29 15:07:22BazarLoader是基于Windows的恶意软件,主要通过电子邮件等方式传播。犯罪分子通过恶意软件后门访问受感染的主机,并对目标域网络环境进行探测,部署Cobalt Strike,绘制网络拓扑图。如果为高价值目标,犯罪分子就会开始横向拓展,部署Conti、Ryuk等勒索软件。
BazarLoader传播方式
2021年夏天,研究人员发现攻击者通过电子邮件传播BazarLoader恶意软件。目前发现三个攻击活动中使用了该恶意软件:
“BazarCall”中使用含有BazarLoader的电子邮件作为初始攻击手段,诱导受害者点击含有恶意软件的文件;
七月初,以侵权为主题的“Sleet Images Evidence.ZIP”中包含了BazarLoader;
7月底,TA551(Shathak)开始通过英语电子邮件传播BazarLoader。
除了这三个主要攻击活动外,研究人员还发现了含有BazarLoader的Excel电子表格,其传播感染方式如下:
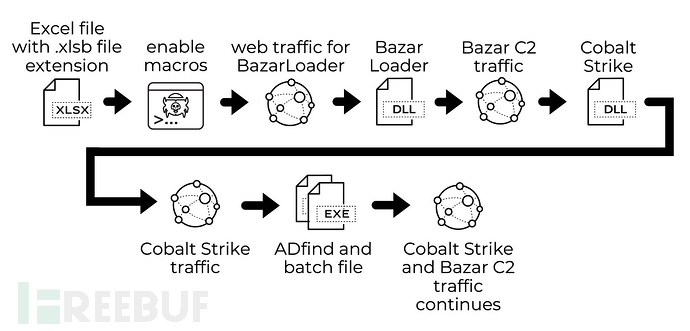
恶意Excel表格
恶意Excel电子表格在8月18日被首次发现的,其最后一次修改日期为8月17日。文件后缀为‘.xlsb’,此文件中包含BazarLoader。下图为恶意Excel截图:
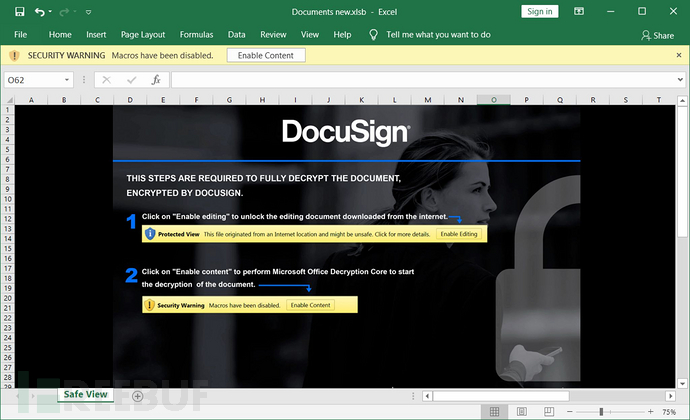
攻击者试图通过利用DocuSign来迷惑受害者。受害者Windows主机上启用恶意宏后,表格中会出现新的sheet,如下图所示:
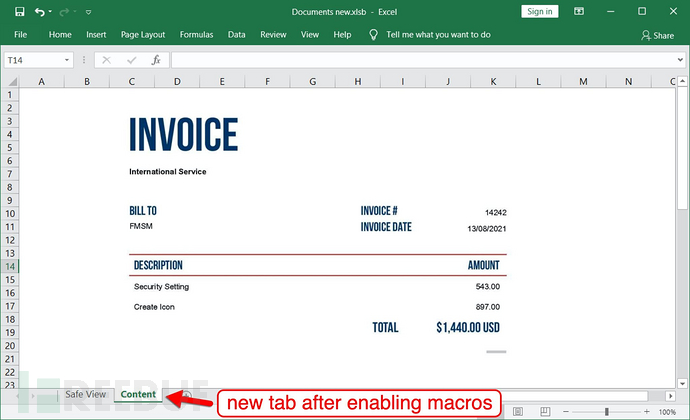
此时恶意代码已经执行,释放出BazarLoader。
BazarLoader分析
恶意文件会从‘hxxps://pawevi[.]com/lch5.dll’中下载BazarLoader的DLL文件,并保存到‘C:\Users\[username]\tru.dll’。
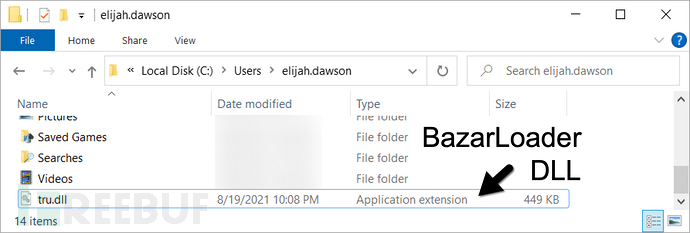
BazarLoader DLL会复制到另一个位置,并修改Windows注册表。
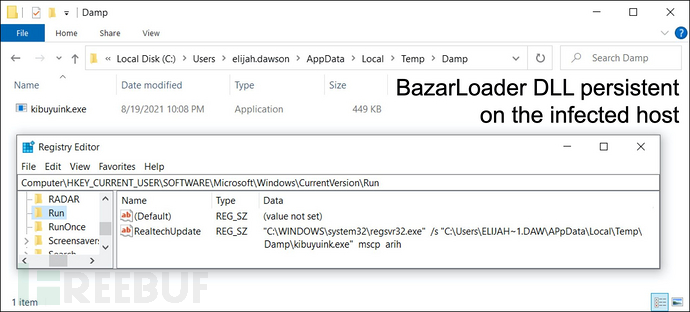
Bazar C2流量
样本BazarLoader通过443端口从104.248.174.225下载BazarBackdoor。BazarBackdoor通过443端口使用HTTPS生成C2活动,传输至104.248.166.170。
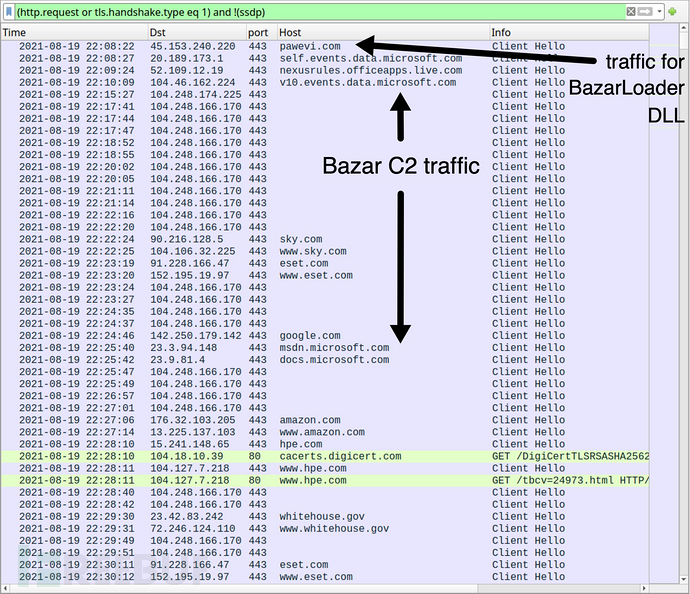
Cobalt Strike恶意活动
BazarLoader感染大约41分钟后,受感染Windows主机通过https与gojihu[.]com和yuxicu[.]com下载运行Cobalt Strike,如下图:
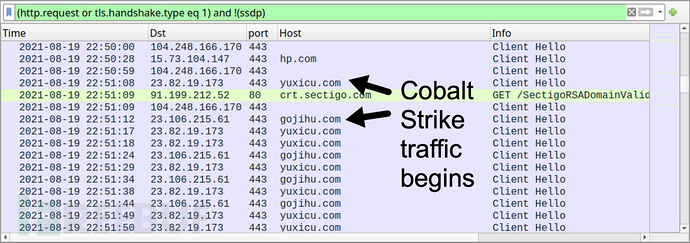
通过Bazar C2获得Cobalt Strike DLL文件,保存到AppData\Roaming目录下,下图为正在运行的Cobalt Strike:
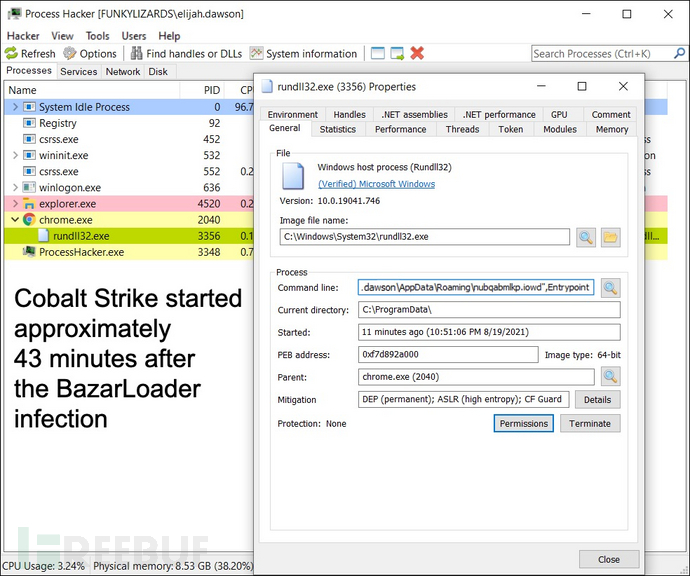
Reconnaissance恶意活动
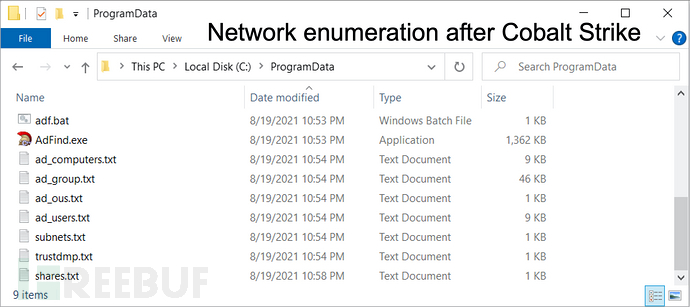
Cobalt Strike运行两分钟后,环境信息采集工具会下载到受感染主机上‘C:\ProgramData\AdFind.exe’。
AdFind是一个命令行工具,攻击者通过批处理文件来运行该工具。下图显示了AdFind位置、批处理文件以及采集结果文件。
Bat脚本内容如下:
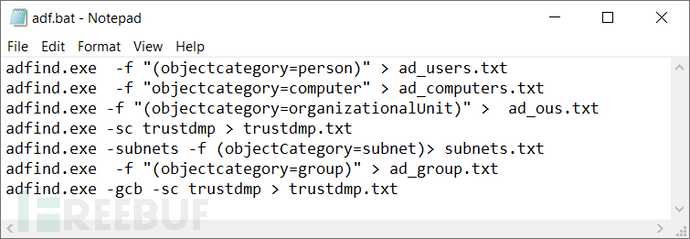
adfind.exe -f “(objectcategory=person)” > ad_users.txt
adfind.exe -f “objectcategory=computer” > ad_computers.txt
adfind.exe -f “(objectcategory=organizationalUnit)” > ad_ous.txt
adfind.exe -sc trustdmp > trustdmp.txt
adfind.exe -subnets -f (objectCategory=subnet)> subnets.txt
adfind.exe -f “(objectcategory=group)” > ad_group.txt
adfind.exe -gcb -sc trustdmp > trustdmp.txt
IOC
BazarLoader Excel SHA256 hash:
8662d511c7f1bef3a6e4f6d72965760345b57ddf0de5d3e6eae4e610216a39c1
Malicious DLL for BazarLoader , SHA256 hash:
caa03c25583ea24f566c2800986def73ca13458da6f9e888658f393d1d340ba1
Online location: hxxps://pawevi[.]com/lch5.dll
Initial saved location: C:\Users\[username]\tru.dll
Final location: C:\Users\[username]\AppData\Local\Temp\Damp\kibuyuink.exe
Run method: regsvr*.exe /s [filename]
Malicious DLL for Cobalt Strike, SHA256 hash:
73b9d1f8e2234ef0902fca1b2427cbef756f2725f288f19edbdedf03c4cadab0
File location: C:\Users\[username]\AppData\Roaming\nubqabmlkp.iowd
Run method: rundll32.exe [filename],Entrypoint
- 以色列国防军禁止高级军官使用安卓手机,强制使用iPhone
- 《公安机关网络空间安全监督检查办法》草案与旧版对比
- 完整议程|12.10-11第二十届中国IDC产业年度大典北京·首钢园启动
- 赛可达实验室携手国际网安盛会,AVAR 2025即将开幕!
- AI全面渗透网络攻击!趋势科技发布2026年六大网络威胁预测
- 2025暴露面管理市场指南:现代风险与暴露面管理平台的演进
- SaaS安全大崩盘!又一起重大攻击,超200家大中型企业数据泄露
- 加紧突破低空智联网建设难题,保障低空运行安全
- 从“高可用”到“高韧性”:企业如何构建不“怕”故障的架构?
- Fortinet CISO预测2026年安全行业:AI重构攻防,CISO以弹性掌舵